CYBER SECURITY CENTRE FACILITIES:
The Cyber Security Centre is composed of several facilities, each facility has a distinguished, yet clear goal.
I. CYBER SECURITY LAB

- Cyber security teaching
laboratory:
a fully pre-equipped laboratory with PCs running Kali Linux Operating System. The PCs have been specially configured and loaded with a variety of ready-to-use tools for hacking and penetration testing. The PC desks are distributed evenly into three groups, and given a color, black, red and blue. Black team represents the administrators, Red color represents the attackers’ team, and Blue color represents the defenders’ team, each team has different duties.
- Offensive Team (Red Team):
responsible for finding weaknesses within the victim devices/services/networks and preparing then launching attacks by exploiting these weaknesses.
- Defensive Team (Blue Team):
responsible for detecting concurring attacks and responding to these incidents as well as preventing them from occurring in the future, and recovering from any potential data loss or system/network damage.
- Black Team (Instructors) :
it represents the centre administrators and the instructors for the teaching laboratory. Their responsibility is preparing the lab, teaching and assessing students. Additionally, the Black team supervises Final Year Project Students (FYPS), prepares lab environment, develops cyber security software tools, and produces research papers within the research centre. This team consists of two members currently, Dr. Basil Alothman and Eng. Shahad Alshaher.
- Education Methods :
The laboratory conducts advanced hands-on education scheme in which the students are divided into two team, the red teamand th e blue team. The students are given tasks and expected to fulfil them based on the duties relevant to their team. Once they complete the tasks, the two groups switch teams. Two main software tools developed by the Cyber Security Centre are used to assess the education process, the tools are: Q8 SIEM, and Q8-CR.
- Q8 SIEM:
born in the Cyber Security Centre in KCST, it is a security Information & Event Management (SIEM) Solution for collecting security log and event data from devices, services, networks, and more. It then produces readable diagrams and charts indicating abnormalities and sends alerts on suspicious security events to the users. Q8 SIEM is used for several purposes including educational, in the cyber security teaching laboratory, mainly by the blue team.
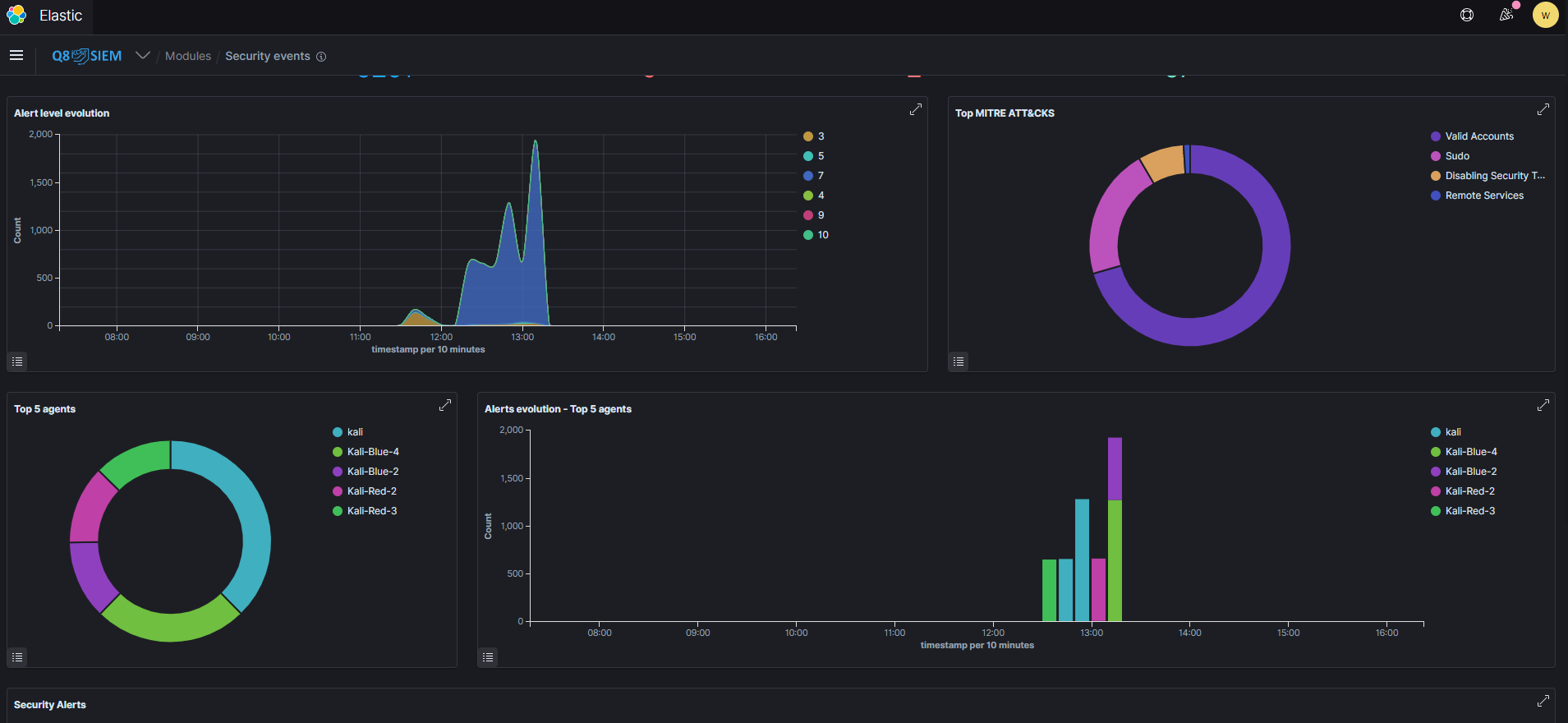
Fig.- Q8SIEM - Kuwait Security Incident and Event Management Dashboard 
Fig.- Q8SIEM Security Logs - Q8-CR:
the Cyber Range was also developed in the Cyber Security Centre. It is a software tool used to assess the process of cyber security education. CR-Q8 is equipped with real-life hacking scenarios, this offers hands-on learning by assessing both the Red team and the Blue team to perform their duties in a protected and isolated environment under controlled conditions. Moreover, it automatically delivers full reports and grading assessments for student performance after each learning session, which can be used by the Black team for reference and final grading.

Fig.- Q8CR - Kuwait Cyber Range Home Paged 
Fig.- Q8SIEM Security Logs - Malware Library:
a physical server installed and used as a Malicious Software (Malware) Library. The library contains a variety of viruses, spyware, trojans, etc. for educational and training purposes.
- Isolated Servers:
Include IOC’s server, malware library server, Cyber Range server.

Fig.- Data Centre and Server Room - Firewalls and IDSs:
To block unauthorized access and only permit authorized users in the network. The intrusion detection system (IDS) is to detect vulnerability exploits against a target device or service.
- Security Operation Centre (SOC):
a centralized function within KCST to monitor and improve the security posture while preventing, detecting, analyzing, and responding to cybersecurity incidents.
- SOC Simulator:
A simulated Security Operations Center (SOC), and Network Operations Center (NOC), used for realistic education, training and competition.
- Network Operation Centre (NOC)
Simulator:
A simulated Network Operations Center (NOC), used for realistic education, training and competition.
- Penetration Testing Activities:
also known as ethical hacking, is an authorized simulated cyber-attack on a computer system, performed to evaluate the security of the system.
- Cyber Threat Intelligence:
Collecting, analyzing and evaluating cyber threat information.
- Cyber Security Incident Response:
Cyber Security Incident Response Team (CSIRT) for dealing with cyber security alerts and warning, incident handling, vulnerability handling, digital Forensics handling, cyber-risk analysis, and intrusion detection.
- Threat Hunting Intelligence
Simulator:
Simulated environment for proactive searching for cyber threats like lurking attacks in the network for education, training and competitions.
- Capture The Flag (CTF) Challenges:
Will be conducted in the lab and hosted in CR-Q8, for education and training.

Fig.- CTF created by the Cyber Centre - Cyber Threat Hunter:
collecting Indicator of Compromise (IOCs) from internal monitoring and using Security Information & Event Management (SIEM) simulator, Intrusion Detection System (IDS), Intrusion Prevention System (IPS) for analysis.
- Cyber Threat Sharing:
Sharing the Centre’s latest IOCs with every organisation/entity in Kuwait through our Kuwait Cyber Threat Exchange.
II. DIGITAL FORENSICS LAB
the centre includes Digital Forensics Labs fully customized and equipped with the needed tools for conducting Digital Forensics Analysis.


III. CENTRE FOR CYBER SECURITY RESEARCH
The Cyber Security Research Centre is the heart of our Cyber Security Centre, where all the cyber research and development are conducted. The goal of the research centre is to produce and publish projects and papers related to cyber security software tools, security vulnerabilities and security solutions, ransomware, malware, threat prevention, and more. Additionally, the research Centre assists students in FYPs related to cyber security.
Works:
- Supervising a PhD students with City, University of London
- KFAS (IoT Security – DDoS) Research Fun
IV. ACADEMIC
- BSc Computer Science
- BEng Computer Engineering
- Other Bachelor Degree Tracks with Cyber Security
- BEng Computer Engineering (New Plan)
-
Track 1: BSc Computer Science and Cyber Security
-
Track 2: BEng Computer Engineering and Cyber Forensic
-
- MSc Cyber Security (City, University of London, De Montfort or Coventry University) as Future plan.
- FYPs: Final Year Projects related to Cyber
Security.
-
Developing a Cyber Incident Exercises Model to Educate Security Teams
-
Enhancing the User Awareness to Secure Social Networks Account
-
Risk reduction of RFID card cloning
-
An Empirical Study on Cloning Ransomware Key Decryptor Using Honeypot Technique
-
Robustness and Security Enhancement for Smart Safe Box Using Private Blockchain Solution
-
Securing Smart cap for blind people
-
Developing Cyber Escape Room for Cyber Awareness
-
Improve the confidentiality of transferring sensitive hardcopy documents using a blockchain tracking system
-
E-Crime Rate Prediction Detector System in Kuwait
-
Enhancing E-Voting System using Blockchain Solutions
-
V. CYBER SECURITY TRAINING CENTRE
The training centre offers courses, special training programs, and certifications for individuals and enterprises. These are conducted on multiple levels ranging from intermediate to advanced, and given by trained cyber security professionals. The figure below shows the currently available certif ications, more training programs and seminars are coming soon:
| S.N. | Course Name | Duration | Audience | Certificate |
|---|---|---|---|---|
| 1 | Cyber AWARE | 2 days | All Public and private employees | CF Level 1 |
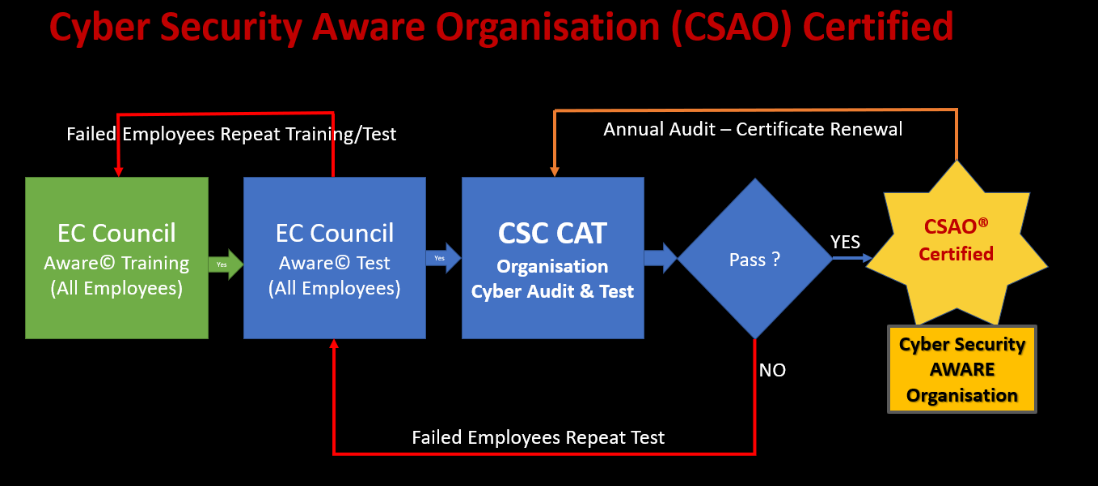
| 2 | Cyber Security AWARE Organisation (CSAO®), figure [1] | Organisations with 75% CF Level 1 certified staff | CF Certified | |
| 3 | Cyber AWARE Plus | 3 days | Managers, Banking sector, Oil and Gas | CF Cert_Plus |
| 4 | Cyber Professionals | 8 days | IT / Cyber Security | EC-Council EH, … |
| 5 | Cyber CxO | 2 days | CxOs, Directors and Board members in Public and private organisations. Top International experts (Andrew Becket, Kevin Jones, …) | BLCS_Cert |
VI. CYBER ACCELERATOR
- Round One Cyber Accelerator
-
About: For the first time in Kuwait, and in collaboration with the British Embassy, KCST arranged CYLON Cybersecurity Accelerator Program that targets experienced employees in IT & Cybersecurity, business owners & graduate students in IT, Science & Engineering. It includes workshops, interactive group sessions, and one to one mentorship. Participants will have a chance to learn from professionals from the UK & showcase their projects to industry leaders.
-
Start Time: 1st of February 2021
-
End Time: 28th March 2021
-
Duration: 8 Weeks
-
- Round Two Cyber Accelerator
-
About: KCST Launching the Cyber Accelerator program round two.
-
Start Time: 24th January 2022
-
End Time: 17th March 2022
-
Duration: 8 Weeks
-
The Accelerator supports the growth of start-up cyber companies who aim to bring new ‘better, faster and cheaper’ security products to market. It aims to support the emerging cyber security industry within Kuwait, encouraging skills, jobs, and growth, see: https://www.ncsc.gov.uk/information/cyber-accelerator



VII. CTF (CAPTURE THE FLAG COMPETITION)
- Haggi Magee CTF: We conduct annual CTF challenge in Kuwait Cyber Security Centre.
- The Cyber Security Centre conducted its first Haggi Magee CFT during KCST’s 2nd annual Cyber Security Week
VIII. HACKERS CLUB
- The Hacker’s Club is a student club that is part of the Cyber Security Centre in Kuwait College of Science and Technology (KCST). And it is a student entity representing a group of our KCST students who share the same vision, mission and passion for initiating activities. It shapes the biggest hackers’ community in Kuwait. Moreover, it is the first hackers club in Kuwait that focuses on cyber security and ethical hacking techniques.
- The Hackers Club vision is to raise cyber security awareness in our community.
- The club has many committees including:
-
Public relation and media committee duties:
-
Announcing events and activities.
-
Managing the club’s social media.
-
Providing club activities coverage on social media.
-
Registering new members.
-
-
Seminars and training committee duties:
-
Creating educational media content (IGTV tutorials, Instagram posts, awareness videos, ...etc.).
-
Organizing cyber security workshops, training programs, and seminars.
-
-
Hackers’ awareness committee duties:
-
Educating the community about latest the security vulnerabilities related to Apps, Operating Systems, etc. and how to be secure from them. .
-
Spreading cyber awareness.
-
-
External event activities participation committee duties:
-
Participating in internal and external competitions, events, workshops, and other activities including international ones.
-
-
Events organizing committee duties:
-
Organizing events and activities.
-
Arranging between different committees.
-
-
Hacker victims committee duties:
-
Helping hacker victims to recover from cyber-attacks.
-
Arranging between different committees.
-
-